Shellshock!
Welcome to Cybersecurity Awareness month! As a person who knows of many cyber-attacks that are not reported, I can say that I would not have imagined what I have seen. While I am concerned by the credit card numbers, and customer information that has been accessed by hackers, I am more concerned by the latest security vulnerability known as Bash Shellshock, especially in the wake of Backoff POS (point of sale) Malware and Heartbleed. The United States Government houses a list of vulnerabilities in the National Vulnerability Database NVD. The vulnerabilities are rated by a set of metrics which includes but is not limited to the impact of the vulnerability found, as well as, remediation efforts. To date, there are over 65000 vulnerabilities listed in the NVD, with 9285 vulnerabilities which have been rated at 9 or 10, with a 10 being the highest rating. Bash Shellshock, which is one of the latest vulnerabilities, received a 10 rating, due to ease of exploitation. Why did Bash Shell receive such a high vulnerability rating? It is important to understand where Bash comes from and how it is interwoven into the very fabric of the Internet, in which not only our laptops connect, but also our iPads, phones and other devices. Bash, which stands for: Bourne Again SHell, Bourne being derived from Stephen Bourne who built a command line, picture shown below, also known as a shell for computer operating systems, mainly UNIX, for Bell Labs in 1977. However, the Bourne SHell is not free and Bash is a Unix SHell that is free. This is important because it ties to free software developed in 1988 known as GNU, which stands for Not Unix, and will be the foundation of many computing technologies today. 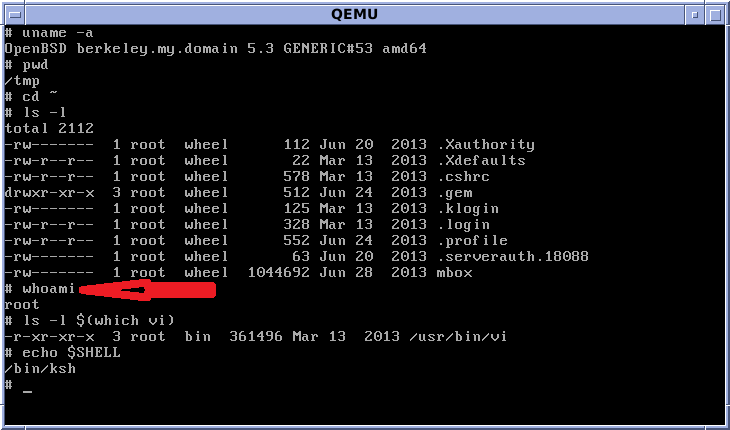 http://en.wikipedia.org/wiki/Bourne_shell GNU was started by Richard Stallman, who quit his job at Massachusetts Institute of Technology MIT, in 1984, so that he could create free software and MIT could not interfere. In the meantime, he created an organization known as the Free Software Foundation, FSF, and his manifesto states that similar to the early years of computers when universities and educational facilities could study software for free, his desire was to recreate the same atmosphere so that operating systems, and any kind of software source code, would be able to be studied for free, and thus free to publish modifications. http://www.fsf.org/ Many engineers would begin developing Bash and create free software, rebuilding Unix that would give birth to GNU, and another flavor of Unix called Linux. A large number of Internet facing properties would be built using GNU Bash. Many Internet products, such as routers, switches, cable boxes, all devices which Internet Service providers use to connect our desktops, laptops, phones, iPad, and notebooks, have GNU Bash interwoven into the computer operating system. Printers, non-traditional network devices, such as dishwashers, refrigerators, smart locks, cameras, digital medical devices, and smart meters, use a Shell command. Recently, our smart dishwasher broke, and in order to diagnose the problem, the company had me enter a few commands which then gave specific tones to my smart phone, and they were able to order the part and send out a technician. The ease of use, instead of having someone to come out and make the diagnostic decision, is a great time saving option. But this time saving option is built upon vulnerabilities, and now these vulnerabilities may very well give a hacker the ability to take over my personal digital devices. And what is even more concerning about the vulnerability is that once the hacker is able to enter one of your devices, they will be able to then proceed to other connected devices in your house, without you even knowing. Open doors, turn off cameras, and even have access to your computers as your logging into your bank. Yes, this is how scary Bash Shell vulnerability really is. In fact, many of the security analyst greatest concerns today are; remote access terminals, RATS, and command and control C&C. RATS and C&C are able to remotely connect to a device on the Internet and then have command and control of the Internet device. We have seen this scenario, but not on the scale that is now possible with the Bash vulnerability. Someone can have command & control over your digital life, which is much worse than someone haven stolen your credit card number or personal information. The hacker can even put in code that would make the digital act on a specific date or when a command was remotely given. In fact, many devices could have a code now inserted into the many internet devices in which it just waits, and waits, and waits, until the command is given. Machines being able to rise up seem like science fiction, but you see, it is not. It is a reality today. The appliances in your house, your cars, your medical devices, all things digital, all things connected, all communicating and understanding commands like the figure shown above which is looking at root access, highlighted by a red arrow. The machine is asking, whoami, and the machine replies back, root. Root access, are the keys to our digital life. Root access in computer language is translated as the creator of our digital world. There are two key areas that you need to be aware of, in trying to protect yourself from cyber security threats: Phishing and Vulnerabilities. Phishing is on the rise, especially as your personal identifying information continues to be breached. The JP Morgan breach consisted of 83 million accounts containing personal information such as email addresses. So, be aware and think before you click on that link! And remember to patch the vulnerabilities that include not only Microsoft, but Adobe and any third party application. The majority of the time, a notification will go out when a patch is needed for vulnerability. Stay safe as you connect.
http://en.wikipedia.org/wiki/Bourne_shell GNU was started by Richard Stallman, who quit his job at Massachusetts Institute of Technology MIT, in 1984, so that he could create free software and MIT could not interfere. In the meantime, he created an organization known as the Free Software Foundation, FSF, and his manifesto states that similar to the early years of computers when universities and educational facilities could study software for free, his desire was to recreate the same atmosphere so that operating systems, and any kind of software source code, would be able to be studied for free, and thus free to publish modifications. http://www.fsf.org/ Many engineers would begin developing Bash and create free software, rebuilding Unix that would give birth to GNU, and another flavor of Unix called Linux. A large number of Internet facing properties would be built using GNU Bash. Many Internet products, such as routers, switches, cable boxes, all devices which Internet Service providers use to connect our desktops, laptops, phones, iPad, and notebooks, have GNU Bash interwoven into the computer operating system. Printers, non-traditional network devices, such as dishwashers, refrigerators, smart locks, cameras, digital medical devices, and smart meters, use a Shell command. Recently, our smart dishwasher broke, and in order to diagnose the problem, the company had me enter a few commands which then gave specific tones to my smart phone, and they were able to order the part and send out a technician. The ease of use, instead of having someone to come out and make the diagnostic decision, is a great time saving option. But this time saving option is built upon vulnerabilities, and now these vulnerabilities may very well give a hacker the ability to take over my personal digital devices. And what is even more concerning about the vulnerability is that once the hacker is able to enter one of your devices, they will be able to then proceed to other connected devices in your house, without you even knowing. Open doors, turn off cameras, and even have access to your computers as your logging into your bank. Yes, this is how scary Bash Shell vulnerability really is. In fact, many of the security analyst greatest concerns today are; remote access terminals, RATS, and command and control C&C. RATS and C&C are able to remotely connect to a device on the Internet and then have command and control of the Internet device. We have seen this scenario, but not on the scale that is now possible with the Bash vulnerability. Someone can have command & control over your digital life, which is much worse than someone haven stolen your credit card number or personal information. The hacker can even put in code that would make the digital act on a specific date or when a command was remotely given. In fact, many devices could have a code now inserted into the many internet devices in which it just waits, and waits, and waits, until the command is given. Machines being able to rise up seem like science fiction, but you see, it is not. It is a reality today. The appliances in your house, your cars, your medical devices, all things digital, all things connected, all communicating and understanding commands like the figure shown above which is looking at root access, highlighted by a red arrow. The machine is asking, whoami, and the machine replies back, root. Root access, are the keys to our digital life. Root access in computer language is translated as the creator of our digital world. There are two key areas that you need to be aware of, in trying to protect yourself from cyber security threats: Phishing and Vulnerabilities. Phishing is on the rise, especially as your personal identifying information continues to be breached. The JP Morgan breach consisted of 83 million accounts containing personal information such as email addresses. So, be aware and think before you click on that link! And remember to patch the vulnerabilities that include not only Microsoft, but Adobe and any third party application. The majority of the time, a notification will go out when a patch is needed for vulnerability. Stay safe as you connect.











