IoT It Is the Data not the Device

The Internet of Things, IoT, is a game changer for businesses that are able to define use cases that will not only provide data critical to their business model, but will strategically help them to quickly identify opportunities.
In order to achieve the results from business, IT administrators need to understand the security challenges and work with the business to help garner the results safely. How can this be done?
A simple definition of the Internet of Things IoT is digital devices that are connected and able to transmit real time data, human interaction not needed. A tire pressure sensor that alerts the driver when tire pressure is low is an example of IoT, as are wearables and Smart Homes. Similarly, the Industrial Internet of Things IIoT, such as manufacturing plants, Industrial Control Systems, gas pipes and valves that are handled by embedded devices that control how much to open a valve via an application on a workstation. I have written about IoT/IIoT and Industry 4.0 and can be read at; http://thatisallfornow.com/?p=19938.
Additionally IoT and IIoT devices architecturally reside in different places due to the industry and business. For example, IIoT has used the Purdue Enterprise Reference Architecture. Figure shown below:
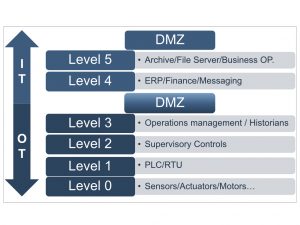
But it is important and today we will define IoT and IIoT as a device that is connected. It will help us to understand how to protect them and more importantly the data, that can be extracted to help business to achieve real time results, the game changer that IoT brings, real time data.
The problem has been visibility and manageability of these devices. How do we manage all the devices and verify that the configuration is correct on the device. Information technologist continue to look for a silver bullet, the solution that can fix it all. But we are looking at the problem in the wrong way. By thinking we have to protect the device, because devices are often a point of compromise, but what we need to think about is protecting the data.
This will align IT departments better to a business model of strategy and growth.
Too often in the business we look to add on, but add on security is not only expensive, but kludgy.
Once the problem has been identified, we can come up with the path that will help business. And traditionally Enterprises have been driven by the device and not the data, when it comes to cyber security.
The device can encompass everything from servers, workstations, laptops, printers, mobile devices, routers, switches, and programmable logic controllers PLC, to name just a few of the challenges that IT face in trying to secure the environment, which has led to a myriad of point solutions, and consoles too many for cybersecurity teams to manage.
Discovery of devices is an area that can lead business into very long projects, which I have personally seen IT and OT paths spending over a year, and come up with the results needed. Today there are many companies that can pull asset information on IIoT and IoT. Asset inventory is very important. What is on my network? And we certainly have seen attacks on devices that can crush assembly lines, but often the focus has been on PLC’s, and other devices that control sensors and actuators. If you are looking at an air gap environment or according to the PERA Layer 0 through 2, it is important to also grab printers and phones that are also connected to the internet. Visually, you will have a better inventory of your assets and what you need to protect. While the risk of some of those assets will be considered low, it is still necessary to know what exists in your environment.
A very difficult challenge for businesses is how to gather information from all these devices. I often find though, that the biggest challenge is the IT Admins and OT personnel. The people have been a very big contributor in both of these groups in not retrieving necessary information for the business.
It helps to start by helping both sides understand the issues that they are facing and agreeing to what is needed. In the past, cyber security professionals have focused on Confidentiality, Integrity, and then Availability, the core information security principles according to ISC2. When it comes to Operational technology, it is about availability, and also the integrity of the data is crucial.
If we do not look at all the devices when reviewing plants, we will be myopic in our focus. The devices to review, when analyzing what is in your environment includes, but is not limited to: Servers, Databases, Workstations, Laptops, Mobile Devices, Printers, Phones, Cameras, Badge Access Readers, and Building Maintenance Systems. While Plants may even have additional devices, it is important to not only know what device is on the network, but the configuration of the device and the data it is sending. This will be key in protecting the assets and help in tracing the data of information.
The future of data provided by IoT applications and how do we secure the data provided by IoT applications? Many companies are consuming the data in AWS, Azure and other cloud providers; but is the critical data secure in the cloud?
In the diagram below is IIoT Cloud Architecture:
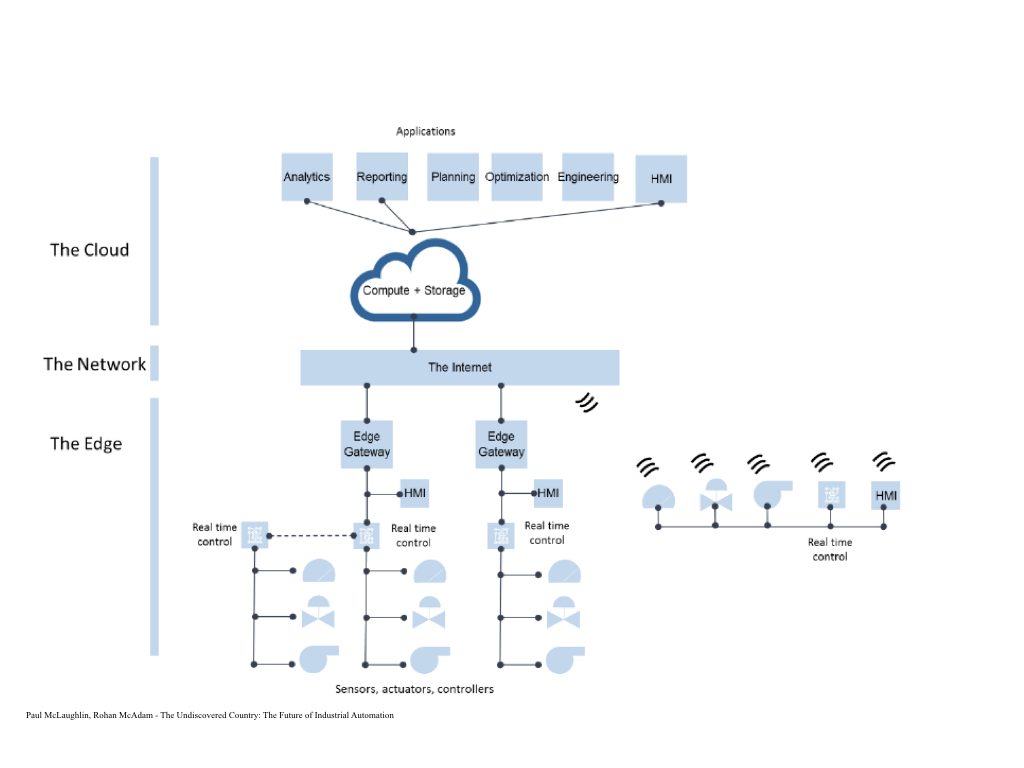
Security for AWS and Azure include firewall settings, private key management and Virtual Private Clouds, but this is not enough to ensure security of assets. While availability is important, the integrity of the data is equally important.
IoT and the development of applications
One of the things that I have often said is that IoT applications are forcing an architecture that is not secure. Security for IoT applications does not have to be an either or situation. Cloud native security as well as IoT has moved to running containerized apps. The whole point of IoT is being able to understand sensors and the data it is able to provide in order to give the business better management. Whether it is a smart building or smart city, all presently are being run by IoT devices that need to be secured, as they push data to the Cloud. We will further explore in our next article. Meanwhile, stay secured and Connected.










